OUR PRODUCTS
Our primary mission is to integrate cyber resilience into enterprises, understanding and overcoming cyber risk.
PRODUCTS
Threat
& Vulnerability Remediation
Find and fix vulnerabilities before they threaten your success.
Prioritizing Vulnerability Remediation: Knowledge is Power
If a chain is only as strong as its weakest link, the same maxim applies to your security system. Spotlighting the exploitable weaknesses present in your environment is a crucial component to keeping your security dynamic and adapting to threats. It’s a necessity that touches all aspects of your organization and requires an awareness of an evolving list of weaknesses, because you never know where or when a breach will happen.
CX Shield's Vulnerability Remediation services guide you through minimizing exploitable security weaknesses by providing risk-based remediation assistance and data-driven metrics that tie into the overall security program. We take an adversarial perspective and a methodological approach to planning, advising and executing remediation of vulnerabilities within your unique environment.
What is Vulnerability Remediation?
Simply put, vulnerability remediation refers to repairing detected weaknesses in an organization’s infrastructure. The process may be as easy as patching software (which is often automated) or as complicated as a major rip-and-replace on a server farm.
Remember: every technical solution has vulnerabilities – or should be assumed to. Some represent an acceptable risk but many don’t. Some appliances – like printers – are low-risk, but others – like your laptop – are high-risk and timely remediation is essential.
PRODUCTS
Cybersecurity Training & Education
Address the Human Element of Your Security Program
Empower Your People to Protect Their Organization
Cybersecurity Education is More Than a Compliance Check Box
No matter how advanced your organization’s security technology is, there will always be risk associated with your workforce. Human risk is difficult to quantify because stakeholders must consider every type of threat: malicious, negligent and compromised. Investing in a holistic program to educate and empower everyone who touches your network will inherently reduce risk by increasing awareness and impacting culture.
CX Shield offers a comprehensive approach to cybersecurity education through both general end-user awareness and role-based training. Meaningful, relevant, current training content establishes a solid foundation for your general user base, while simulated phishing campaigns provide insight and create opportunities for risk mitigation.
Historically, security awareness training programs involved an annual window with content driven by compliance requirements. With the evolving threat landscape, this approach is not enough. Each employee and contractor is a component of your defensive posture, and CX Shield Cybersecurity Education programs not only address areas of need but also engage users to embrace and acquire meaningful behavior change.
Learn
We work with your stakeholders to identify appropriate general end-user and role-based training to provide meaningful business impacts and personal relevance to end-users.
Experience
We’ll help create an environment of awareness, including formalized training with reinforcement materials like newsletters, posters, digital images and simulated phishing campaigns.
Transform
Our cyber education program is more than just content – it’s a strategy. We help you transform your organization’s culture into one of awareness, responsibility and ownership through positive behavior change.
PRODUCTS
Manage Cyber Risk to Ensure Compliance
Take the guesswork out of regulatory requirements

Don’t Let Regulations Slow You Down
Regulations and industry standards are complex and ever-changing. How do you establish organizational objectives alongside a regulatory environment that could change in a year? Your approach to compliance should not only protect your organization today but implement future-proof technology and solutions that contribute to long-term success.
It can be challenging to unite privacy, risk management and compliance programs into a single strategy that doesn’t feel like a barrier to business objectives. Organizations without formal programs or dedicated headcount often hesitate to get started or take the next step.
Navigate Compliance with Ease
CX Shield helps clients reduce their compliance burden by identifying focus areas based on their regulatory environment to create a compliance strategy that contributes to business progress. We leverage proprietary methodologies and industry best practices proven to strengthen risk mitigation, brand protection and stakeholder trust and engagement.
Through industry-leading experts and technology partnerships, we can implement and optimize solutions to help scale or enhance program capabilities to meet current and future standards.
PRODUCTS
Adopting Zero Trust
Let CX Shield Be Your Guide on Your Zero Trust Journey
What Is Zero Trust?
Zero Trust is an information security model based on the principle of maintaining strict access controls by not trusting anyone or any action by default, even those already inside the network perimeter.
Instead, each transaction is evaluated for need and risk. It combines network and application micro-segmentation and identity and access management platforms to verify access and authorization, and it allows for more granular access control and machine/application-specific policies. It also employs multifactor authentication, IAM, orchestration, analytics, encryption, scoring and file system permissions, plus governance policies such as giving users the least amount of access they need to accomplish a specific task.
So, sometimes, it’s best to assume the worst. Zero Trust security solutions protect networks, applications and data based on the concept of “never trust, always verify.” In a Zero Trust model, identity is the core security control used by security teams that “assume breach” because any user or device is a potential threat actor.
PRODUCTS
Zero Trust Segmentation
Assume breach. Minimize impact. Increase resilience.
Welcome to the new era of Zero Trust Segmentation
Unlike prevention and detection technologies, ZTS contains the spread of breaches and ransomware across the hybrid attack surface by continually visualizing how workloads and devices are communicating, creating granular policies that only allow wanted and necessary communication, and automatically isolating breaches by restricting lateral movement proactively or during an active attack. ZTS is a foundational and strategic pillar of any Zero Trust architecture.
It seems everything has to be connected to the internet these days. Convenient to many, but a significant challenge for CISOs, security, and IT teams. IT environments are moving from on-premises to a hybrid, cloud-first, hyper-connected landscape. Digital transformation is dramatically expanding the attack surface, and attacks like ransomware are more pervasive than ever. In the past two years alone, 76% of organizations were attacked by ransomware, and ransomware attacks occur every 11 seconds. All these factors are increasing risk.
Breach containment.
The new paradigm.
76%
of organizations
In the past 2 years, 76% of organizations were attacked by ransomware
11
seconds
Ransomware attacks occur every 11 seconds
Speed, sprawl, and volume of attacks are the culprits
Modern hybrid IT is messy, and it creates new risks every day. The sprawl of hybrid IT is introducing significant gaps in the attack surface. Attackers are feasting on a landscape of multiple clouds, endpoints, data centers, containers, VMs, mainframes, production and development environments, OT and IT, and whatever lies around the corner.
All these apps and systems are continually creating new attack vectors as they communicate with each other, and with the internet, in ways you might never have imagined...but attackers have. This relatively new interconnectivity is how attacks move quickly from the initial breach to their ultimate target.
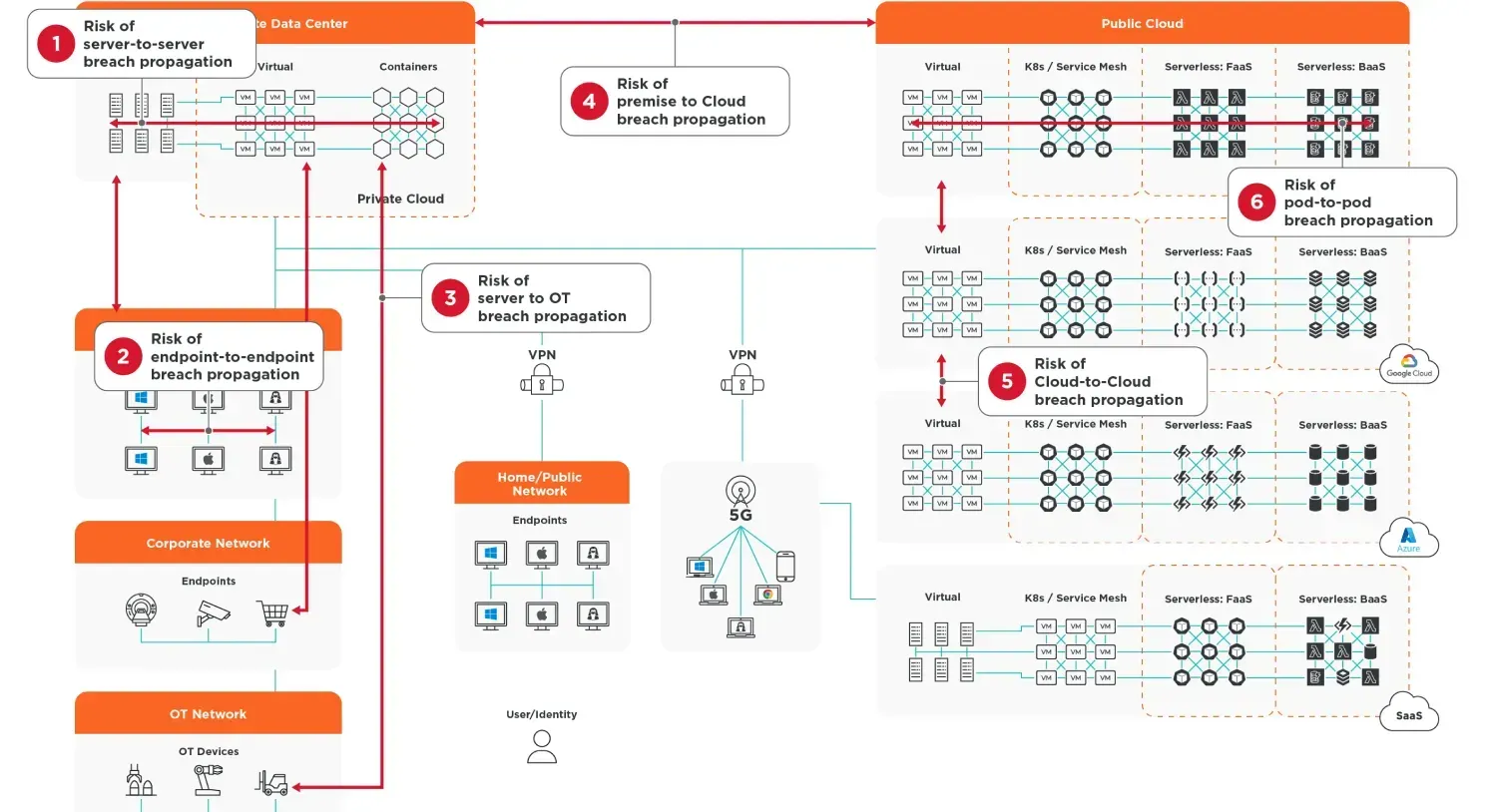
2000s and 2010s
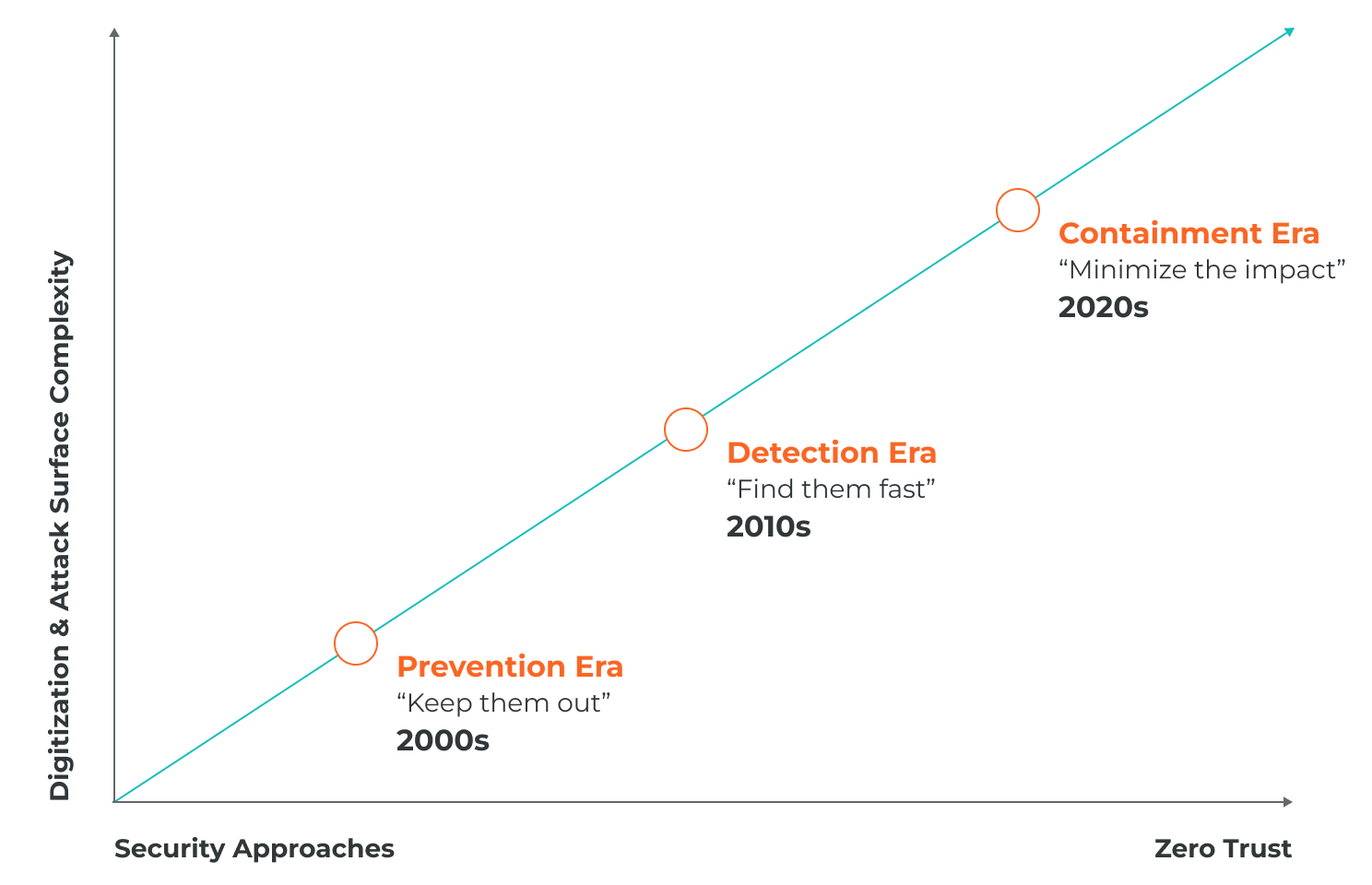
The tools traditionally used for security cannot solve this new problem. In the prevention era of the early 2000s, the ethos was “keep them out” by building a moat. However, a series of high-profile breaches in the early 2010s highlighted the fact that attackers move fast and leverage new attack vectors and led to the detection era and a mantra of "find them quickly."
Prevention and detection tools like firewalls, EDRs, or SIEM only give surface-level visibility into traffic flows that connect these applications, systems, and devices that are communicating across IT. They were not built to contain and stop the spread of breaches.
2020s and beyond
The movement to Zero Trust and containment is fueling a tectonic shift in security approaches and technologies we haven’t seen for over a decade. We’ve now entered the new era of containment. Since the attack surface continues to rise in complexity, organizations are rapidly embracing the Zero Trust principle of “assume breach” — changing the focus to stopping the spread and minimizing the impact of a breach.
It’s time for a new approach and technology which moves us from the “find and fix” mindset to the ”limit and contain” reality and applies the principles of Zero Trust to focus on breach containment, not just prevention and detection.
One platform. One console. Any environment.
The CX Shield Zero Trust Segmentation (ZTS) Platform is the industry’s first platform for breach containment.
Scalable yet easy to use, CX Shield ZTS provides a consistent approach to microsegmentation across the entire hybrid attack surface — from multi-cloud to data center to remote endpoints, from IT to OT. With Illumio ZTS, organizations can quickly and easily see risk, set policy, and stop the spread of breaches.
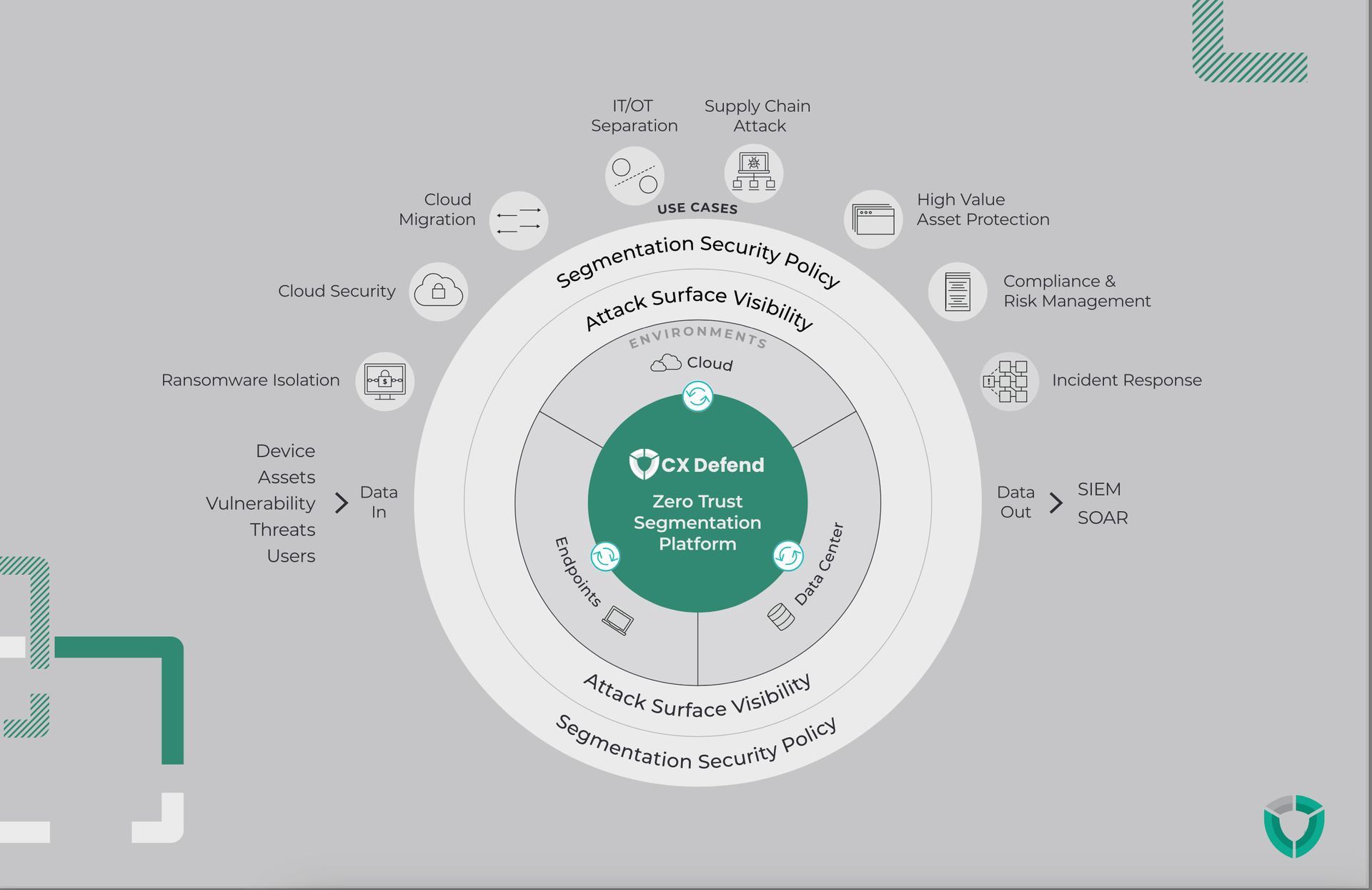
Protect workloads and devices with the industry's first platform for breach containment
See risk
See risk by visualizing all communication and traffic between workloads and devices across the entire hybrid attack surface. For example, which servers are talking to business-critical apps, and which applications have open lines to the internet.
Set policy
With every change, automatically set granular and flexible segmentation policies that control communication between workloads and devices to only allow what is necessary and wanted. For example, restrict server-to-app communications, dev to prod, or IT to OT.
Stop the spread
Proactively isolate high-value assets or reactively isolate compromised systems during an active attack to stop the spread of a breach. For example, see how a global law firm instantly isolated a ransomware breach.
Stop ransomware attacks in ten minutes, 4x faster than detection and response alone
2.1x more likely to have avoided a critical outage during an attack in the past two years
2.7x more likely to have a highly effective attack response process
Save $20.1 million in annual downtime costs
Avert 5 cyber disasters annually
Accelerate 14 more digital transformation projects
The power of Zero Trust Segmentation
The business results speak for themselves
Organizations leveraging CX Shield ZTS Platform:
CX Shield ZTS Platform is adopted by organizations of all sizes to help solve some of the hardest security challenges.
- ZTS helps organizations ringfence and protect high-value applications and data by restricting access to only that which is critical and necessary.
- ZTS helps organizations migrate to the cloud by visualizing hybrid and multi-cloud application workload communications that highlight major security gaps across dispersed architectures.
- ZTS provides complete visibility of assets and traffic flows to overcome incomplete or fragmented visibility into risk.
- ZTS is used to create boundaries between IT and OT systems to stop the spread of OT attacks that easily come in from IT.
- ZTS is used in incident response to defend against active ransomware attacks in minutes.
- ZTS automates effective and consistent cloud security enforcement across hybrid and multi-cloud deployments.
